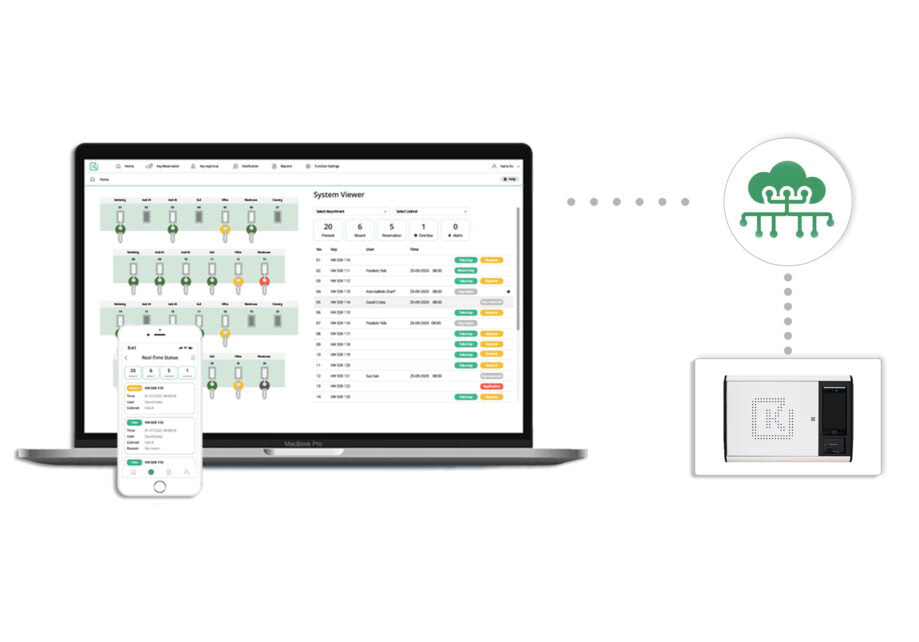
Real-Time Control from Any Device
Keylongest WEB is a secure, browser-based management platform that lets you monitor and control your key systems from any device - smartphone, tablet, or PC - without the need for software installation. With an intuitive interface, real-time updates, and encrypted communication, it puts complete system visibility at your fingertips.
- Real-time key status and activity logs
- Full reporting and audit trails
- Automatic alert emails for key events
- Easy integration with third-party systems
- SSL-encrypted for secure data transmission
Stay connected to your key systems anytime, anywhere - with the simplicity of the cloud.
Features
There are 3 roles by default and customized roles with varying levels of authorization in the web software. These range from simple report readers to admin.
Apply time-based restrictions to specific users, allowing access only during approved hours or shifts. Perfect for managing contractors, shift workers, or shared spaces with limited access windows.
In the software you can see the instant status of any of your keys in real time, whether they are being used, and who holds them.
Can be set on any key to enforce its return by a certain time. Will also generate an alert if the key isn’t returned on time. There are two types of time limit: time duration, and time schedules.
It’s allowed to remove keys or return keys remotely by off-site administrators. Will also can lockdown the key remotely.
For unplanned visits to some important keys, users should provide a detailed description, including the reason, purpose, or explanation for which the visit occurred
Can be set up to alert managers if a specific action occurs, such as curfew is overdue or a door is left open.
This allows users to reserve items for a specific period of time. For example; a company pool car may be booked out for a set day for a specific individual, ensuring that the keys are not able to be accessed or taken by other members of staff.
Multi-factor authentication (MFA) is a security method that requires users to provide at least two authentication factors to prove their identity and gain access to a key.
For certain keys or key sets that are highly-sensitive, compliance regulations may require signatures from two or three individuals, one each from three separate departments.
The system allows managers to maintain permissions from both employee and key views.
Multiple systems are connected for use, data is shared across multiple ends, achieving maximum scalability